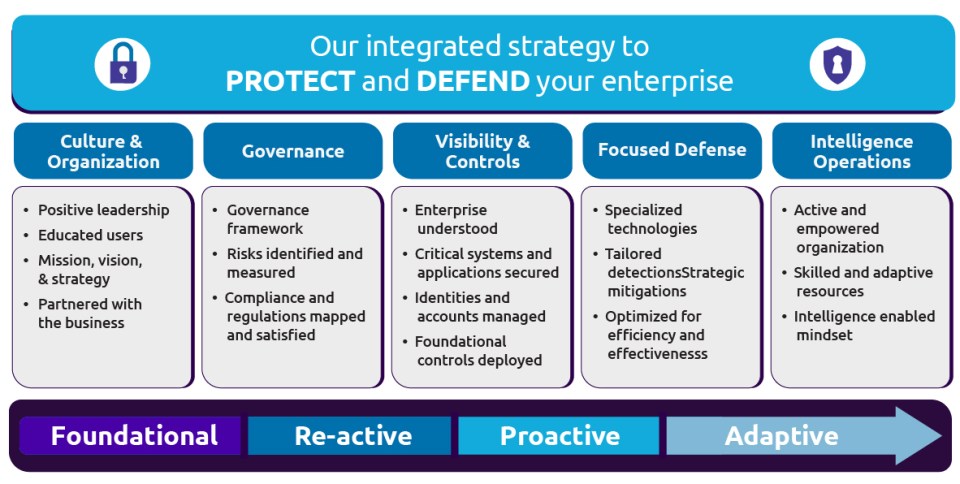
Elements Of Cyber Security Strategy

Behavioral analytics to detect abnormal.
Elements of cyber security strategy. A firewall to monitor and control network traffic. I repeatedly encounter cases where companies spend lots of money on physical access protection but leave all doors wide open when it comes to e mail. It protect websites and web based application from different types of cyber security threats which exploit vulnerabilities in an source code. Cybersecurity is a complex and worrisome issue for all organizations.
We have the first two elements of a long term cyber strategy defined. Proactive network security is an essential element of any organization s cybersecurity. An effective cybersecurity risk management plan should include five foundational items which in turn will jump start the organization to go down the right path. Such a strategy needs to provide an organisation with actionable intelligence and must encompass the very latest attack vectors such as cross platform attacks.
Implementing a strong cybersecurity strategy can only be achieved with a robust security team in place. Application security is the first key elements of cybersecurity which adding security features within applications during development period to prevent from cyber attacks. An effective cyber security strategy must work across an organisation s security measures. Pa brings together world class capability in a range of key disciplines such as software and network security scada and process control.
From system hardening and network zoning to active security monitoring yet companies can protect themselves even against such professionally prepared attacks. Three key elements of cybersecurity strategy. Focus on the right tools. It is also possible to make smart interventions in key areas of vulnerability to boost overall cyber security.
The national security agency nsa developed and published a technical extension of the director of national intelligence cyber threat framework ctf to provide specific and actionable steps and. Top cyber security companies. For a plan to be effective it needs to have the five elements described here. It has never been more critical to recruiting wisely.
Therefore an organization should be aware of that. Below mentioned are three critical aspects to avoid cyber incidents. Network security guards against malicious attacks such as those listed above. Network security often includes the following.
The risk profile of an organization can change anytime. There are five key components to any security strategy that need to be included regardless of how comprehensive and thorough the planning process. This allows it to beat security measures that require payments be confirmed using a mobile device. If someone wants to enter the building.